CYSE 250
Basic Cybersecurity Programming and Networking Course
The course introduces cybersecurity-centric programming and networking concepts. Students develop problem-solving skills by using the high-level programming language of Python and learning the fundamentals of network protocols. It is the technical base for students to take cybersecurity major courses.
Research Paper
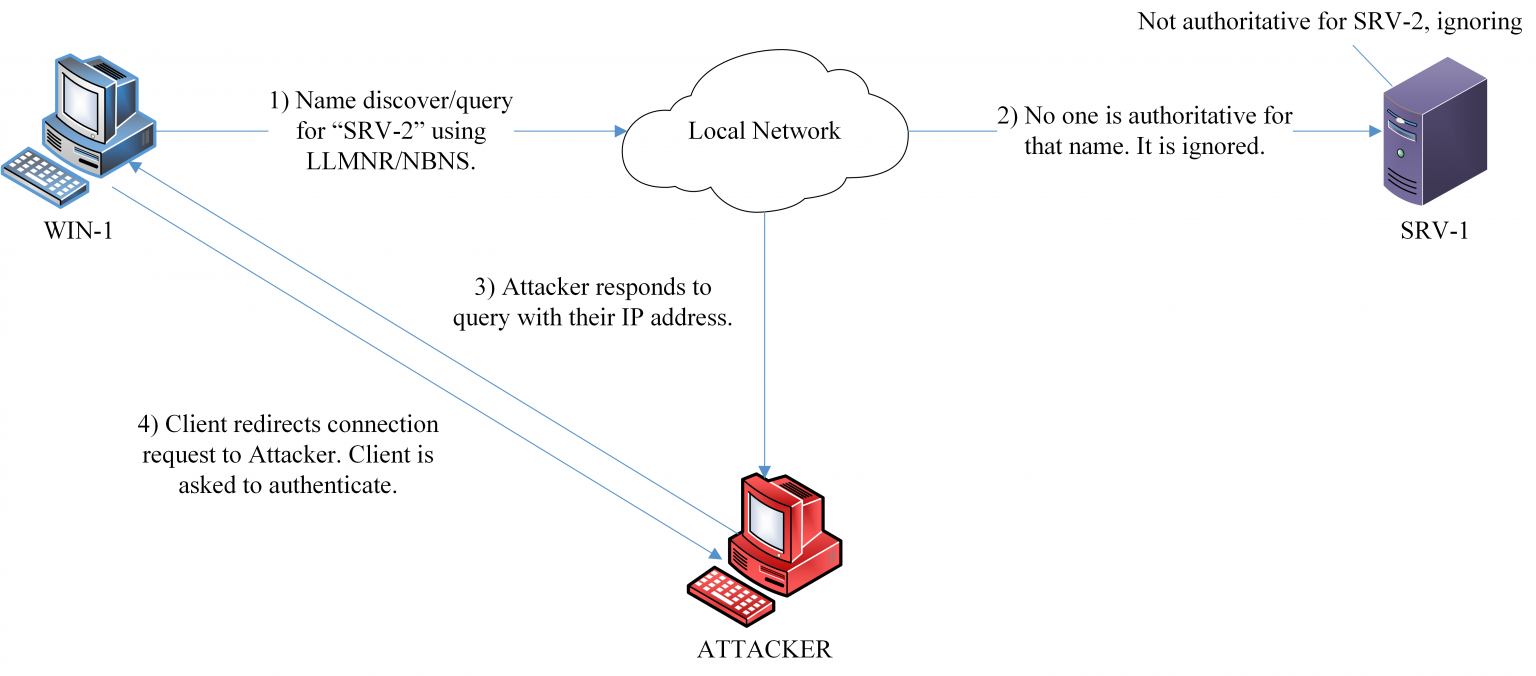
Hijacking of the Windows LLMNR/NBNS name resolution process for credential harvesting.
The following research paper explores an Adversary-in-the-Middle (Man-in-the-Middle or on-path) attack that exploits the weaknesses of the Windows Name Resolution Services for privilege escalation and lateral movement on an already compromised network. In my paper, I discovered Windows systems would typically fall back on alternative name resolution services when DNS fails to yield results. These alternatives – Link-Local Multicast Name Resolution and NetBIOS Name Service – will normally be enabled by default for Windows to use. While both are useful in certain situations, their operation may open a system to poisoning attacks that redirect connections to another system. Once redirected, an attacker can run rouge authentication services to capture user credentials for offline cracking or use them in relay attacks to gain access into a target system.
Keeping to the purpose of learning Python and using it effectively in cybersecurity work, the research paper covers a Python-based pen testing tool called Responder that can perform every stage of the attack, including a particular relay attack called SMB relay. I used the tool, my virtual cybersecurity lab, and the virtual labs offered through ODU’s MOVE to understand every attack stage. The paper also allowed me to delve into the Python language to know how the Responder tool worked, what the code was doing, and how it can be modified or spurn the creation of similar tools for cybersecurity research and work.
Course Reflection
This course allowed me to take an in-depth look into cybersecurity-centric programming and learn how to apply it to the Cybersecurity field. Python as a high-level language is perfect for this Cybersecurity work as it is flexible, easy to master the basics, and scalable to meet the task at hand. As a fledgling Cybersecurity professional, I must know how to devise and create custom scripts and tools for handling unique challenges that off-the-shelf pre-written tools cannot solve. With the knowledge I have learned in the course, I can encounter a given problem, apply the Python language, and create a tool that can solve it.